SOC 2 (System and Organization Controls 2) is a security framework developed by the American Institute of CPAs (AICPA). Its purpose is to assure your customers that you have strong internal controls to manage and protect their data securely.
It is one of the most widely recognized and crucial security standards for service organizations that store, process, or transmit customer data, such as:
- SaaS companies
- Cloud service providers
- Fintech and payment processors
- Managed Service Providers (MSPs)
Visit now to know more- What is SOC 2
What Does SOC 2 Compliance Mean?
Achieving SOC 2 compliance means that an organization has implemented controls that meet the rigorous Trust Services Criteria (TSC) and has successfully undergone an official audit by an independent CPA firm.
This process demonstrates a commitment to security and is often a mandatory requirement for securing enterprise contracts.
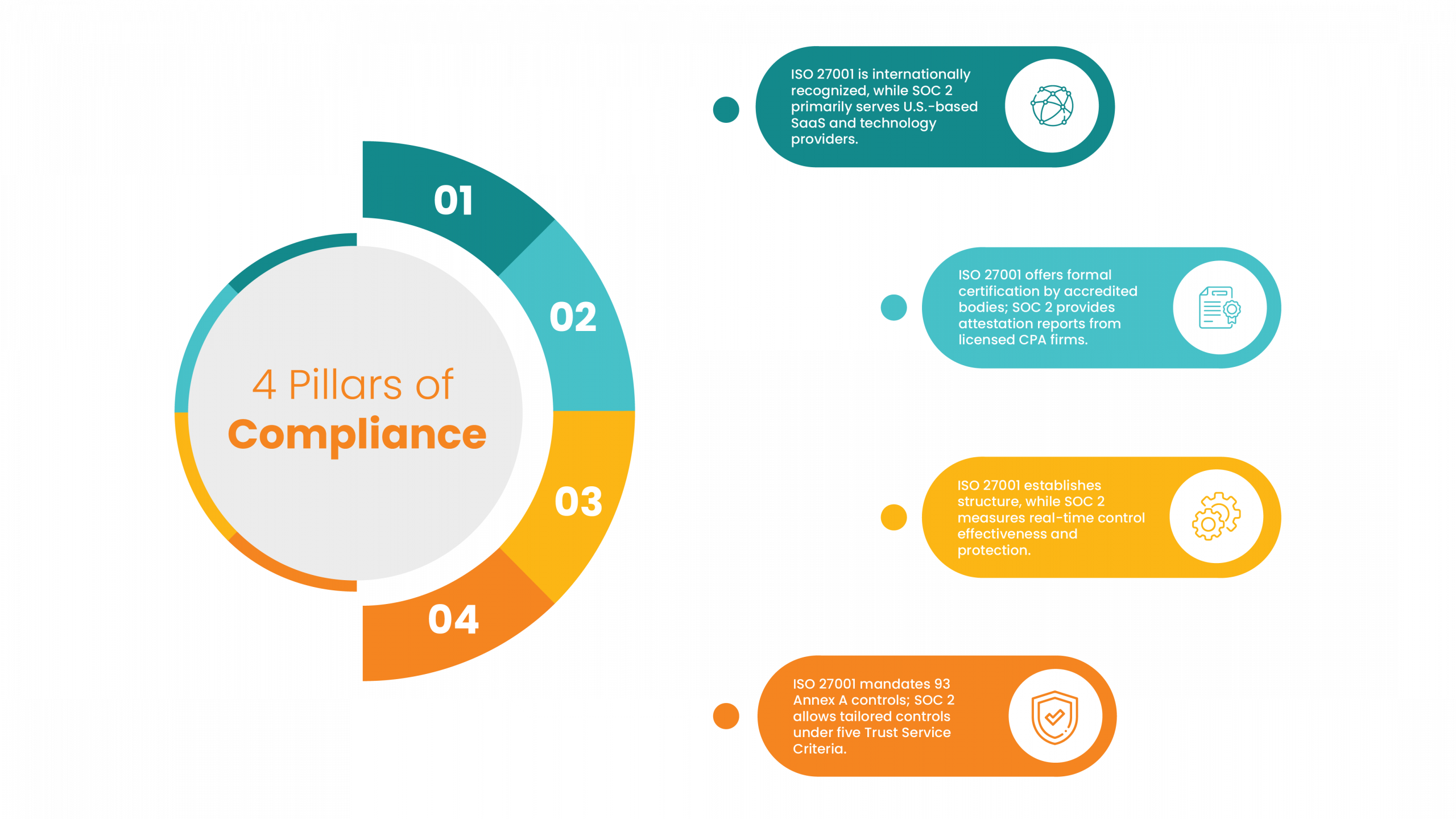
Is SOC 2 the Same as ISO 27001?
No, they are not the same:
| Feature | SOC 2 | ISO 27001 |
| Standard Origin | American (AICPA) | International (ISO/IEC) |
| Deliverable | Audit Report/Attestation | Certification |
| Focus | Controls and criteria based on the 5 TSCs. | Formal Information Security Management System (ISMS). |
| Controls | Flexible—you define your controls to meet the criteria. | Prescriptive—requires a set of mandatory controls (Annex A). |
Companies often pursue both for global credibility and comprehensive security management.
2. SOC 2 Types: Type I vs. Type II
There are two primary types of SOC 2 reports, and they differ based on the time period they cover:
| Feature | ✔️ SOC 2 Type I | ✔️ SOC 2 Type II |
| Evaluation Focus | Design suitability of controls. | Design and operating effectiveness of controls. |
| Time Period | A single point in time (a snapshot). | Over a period of time (typically 3–12 months). |
| Value | Useful for early-stage companies or initial due diligence. | More trusted and usually required by enterprise customers. |
| Effort/Cost | Faster and less expensive. | More intensive, more time, and more costly. |
Note: SOC 1 reports cover controls related to an organization’s internal control over financial reporting (ICFR). SOC 2 reports cover controls related to data security and trust.
What Are the 5 SOC 2 Principles?
The SOC 2 framework is built around five areas, known as the Trust Services Criteria (TSC), which are evaluated during the audit. The Security principle is mandatory for all SOC 2 reports.
| Principle | Description | Example Control |
| 1. Security (Required) | Protecting systems and data from unauthorized access, disclosure, or damage. | Multi-Factor Authentication (MFA), Firewalls, Intrusion Detection. |
| 2. Availability | Ensuring the system is available for operation and use as agreed upon (e.g., uptime). | Disaster Recovery/Business Continuity Plan, System Monitoring. |
| 3. Confidentiality | Protecting information designated as confidential (e.g., intellectual property, internal price lists) from unauthorized disclosure. | Access controls on internal data, Data Encryption (in transit/at rest). |
| 4. Processing Integrity | Ensuring system processing is accurate, complete, valid, and timely to meet business objectives. | Quality assurance procedures, error detection and correction controls. |
| 5. Privacy | Protecting Personal Identifiable Information (PII) according to the organization’s privacy notice and relevant regulations. | Secure disposal of personal data, controlled PII collection and use. |
The SOC 2 Compliance Checklist (Step-by-Step)
Achieving compliance involves a structured, multi-phase effort, especially for a more rigorous Type II report.
Phase 1: Planning & Assessment
- Define Scope:
- Choose the specific systems, services, and data flows to be included.
- Select the Trust Service Criteria (TSC) relevant to your service (Security is mandatory, others are optional but recommended based on customer commitments).
- Conduct Risk & Gap Assessment:
- Identify potential risks to the in-scope systems (e.g., unauthorized access, operational errors).
- Perform a Gap Analysis to compare your existing controls against the chosen TSC and identify missing policies or controls.
- Establish Mandatory Policies:
- Draft and formally approve essential written policies, including Information Security Policy, Access Control Policy, Incident Response, and Change Management.
Phase 2: Implementation & Evidence Collection
- Implement Controls & Remediate Gaps:
- Execute the necessary technical and procedural controls identified in the gap analysis.
- Examples: Implementing MFA across all systems, enabling continuous audit logging, performing penetration testing, and conducting security awareness training.
- Collect Evidence:
- Gather artifacts to prove your controls are designed and operating effectively over the review period.
- Examples: System logs, configuration settings, policy acknowledgements, HR records, and vendor SOC reports.
Phase 3: Audit
- Conduct a Readiness Assessment (Optional but Recommended):
- A pre-audit check by a consultant to identify and fix any last-minute issues before the formal audit begins.
- Undergo the SOC 2 Audit:
- A licensed CPA firm performs the formal audit, which includes:
- Reviewing your System Description and policies.
- Performing Walkthroughs and interviewing personnel.
- Testing controls (especially for Type II reports).
- A licensed CPA firm performs the formal audit, which includes:
- Receive the Final Report:
- The auditor issues a final SOC 2 report, providing an opinion on the design (Type I) and/or operating effectiveness (Type II) of your controls.
5. SOC 2 Certification Cost (Typical Ranges)
The total cost for SOC 2 compliance is a significant investment and depends heavily on company size, complexity, and the type of report being pursued.
Click here to view cost- SOC 2 Certification Cost
- Why SOC 2 Matters & Who Needs It
Why it Matters:
- Builds Customer Trust: Provides an independent, professional assurance that your security controls are not only documented but are actively working.
- Enables Enterprise Sales: A SOC 2 Type II report is often a non-negotiable minimum requirement for large-scale enterprise contracts and vendor management.
- Strengthens Security Posture: The preparation process forces the organization to improve and formalize its own risk management and operational discipline.
Who Needs It:
If your business provides services where you collect, store, or process customer data—especially in the cloud—SOC 2 is likely mandatory for your growth. This includes:
- SaaS Platforms
- Cloud Hosting & Infrastructure
- Data Analytics/Big Data Companies
- Fintech & Payment Processors