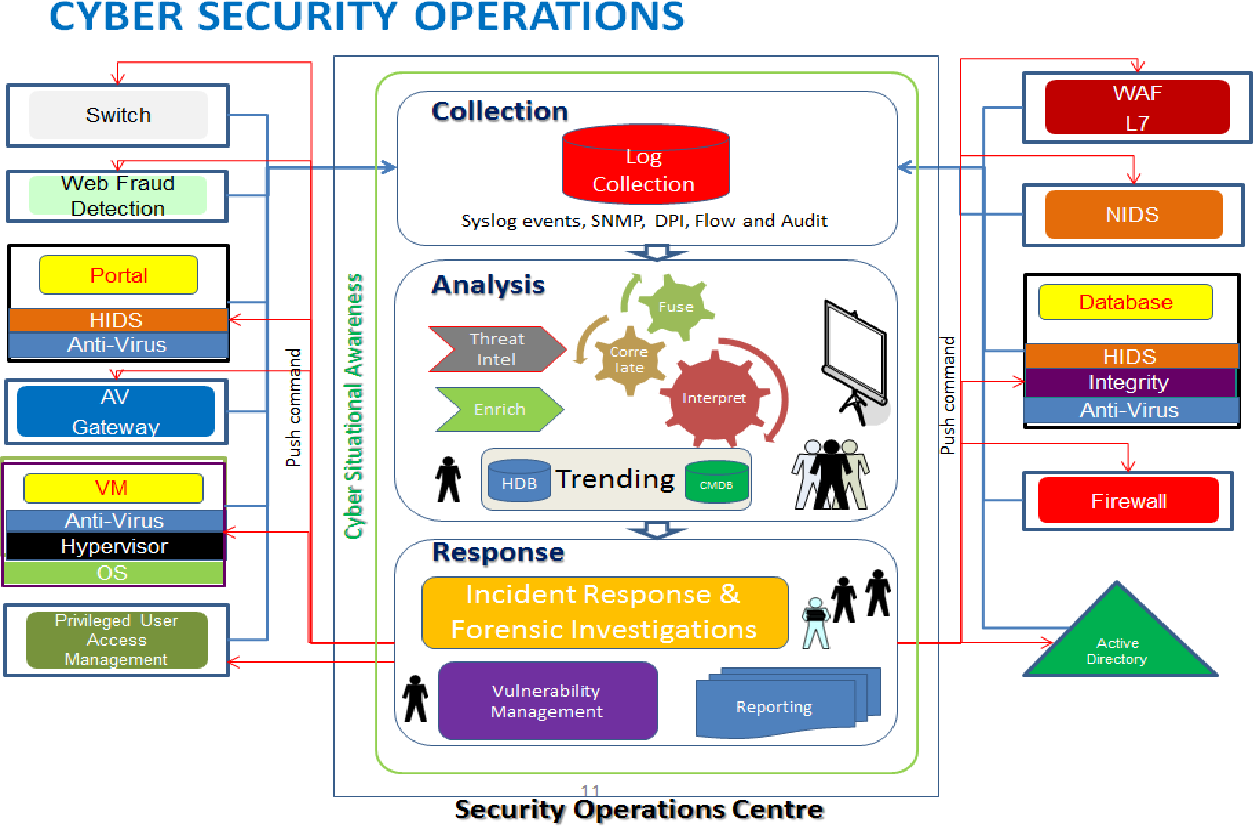
Introduction to Security Operations Centers (SOCs)
A Security Operations Center (SOC) is a centralized unit that monitors, detects, and responds to cybersecurity threats within an organization. It serves as the nerve center for cybersecurity defense, integrating advanced technology and skilled personnel to safeguard digital assets. SOCs analyze vast amounts of data from various sources like network traffic, logs, and endpoints to identify suspicious activities. They operate 24/7 to ensure continuous protection against cyberattacks, malware, and insider threats. The primary goal is to minimize damage, prevent breaches, and ensure compliance with security standards. As cyber threats evolve rapidly, SOCs employ cutting-edge tools such as Security Information and Event Management (SIEM) systems, threat intelligence platforms, and automation to enhance their capabilities. An effective SOC is vital for organizational resilience in an increasingly digital world.
Functions and Responsibilities of a SOC
A SOC performs several critical functions to maintain organizational cybersecurity. Its core responsibilities include real-time monitoring, threat detection, incident response, and vulnerability management. The team continuously analyzes security alerts generated by various tools to identify anomalies. When threats are detected, SOC analysts initiate incident response protocols to contain and mitigate damage. They also conduct forensic investigations post-incident to understand attack vectors and improve defenses. Regular vulnerability assessments help identify potential weak points before exploitation. Additionally, SOCs ensure compliance with regulatory standards such as GDPR, HIPAA, or PCI DSS. The team collaborates with other departments to implement security policies and educate staff on best practices. Overall, the SOC acts as the frontline defense, proactively managing risks and maintaining organizational security posture.
Key Technologies Used in Modern SOCs
Modern SOCs leverage a variety of advanced technologies to enhance their threat detection and response capabilities. Security Information and Event Management (SIEM) systems aggregate and analyze logs from diverse sources, providing comprehensive visibility into network activities. Endpoint Detection and Response (EDR) tools monitor individual devices for malicious activity and provide automated responses. Threat intelligence platforms gather and correlate data from global sources to identify emerging threats. Security Orchestration, Automation, and Response (SOAR) tools enable automated incident handling, reducing response times. Firewalls, intrusion detection/prevention systems (IDS/IPS), and antivirus solutions form the technological backbone. Additionally, artificial intelligence (AI) and machine learning (ML) algorithms help identify patterns and anomalies that might escape traditional detection methods. These technologies work together to create a proactive, efficient, and adaptive cybersecurity environment within the SOC.
Importance of Skilled Personnel in a SOC
A SOC’s effectiveness heavily relies on its skilled personnel who possess a deep understanding of cybersecurity threats and defense mechanisms. Analysts, engineers, and incident responders form the core team responsible for monitoring and managing security events. They interpret complex data, investigate incidents, and develop mitigation strategies. Skilled SOC personnel stay updated with the latest attack techniques, vulnerabilities, and security tools through continuous training and certifications such as CISSP, CEH, or SANS. They also collaborate with threat intelligence teams and management to ensure security policies align with organizational goals. The human element is crucial for contextual analysis, decision-making, and handling sophisticated threats that automated systems may miss. Building a talented, well-trained team ensures rapid detection, effective response, and ongoing improvement of the organization’s cybersecurity defenses.
Challenges Faced by Security Operations Centers
Despite technological advancements, SOCs face numerous challenges in maintaining optimal cybersecurity defense. One major issue is the overwhelming volume of security alerts, many of which are false positives, leading to alert fatigue among analysts. Sophisticated cyberattacks like zero-day exploits are difficult to detect and require advanced skills and tools. Limited staffing and skills shortage further strain SOC operations, causing potential delays in incident response. Evolving threat landscapes demand continuous updates to security protocols and technologies. Budget constraints can restrict access to cutting-edge tools or training. Additionally, integrating disparate security tools into a cohesive system is often complex, affecting efficiency. Managing insider threats and ensuring compliance with regulatory standards also add layers of complexity. Addressing these challenges requires strategic planning, automation, and ongoing personnel development.
Future Trends in Security Operations Centers
The future of SOCs is poised to be shaped by emerging technologies and evolving cybersecurity needs. Automation and AI will increasingly handle routine tasks, allowing analysts to focus on complex threats requiring human judgment. Cloud-based SOCs are gaining popularity for scalability and cost-efficiency, especially for organizations with remote or distributed operations. Integration of threat intelligence feeds will improve proactive threat hunting capabilities. Zero Trust architectures and advanced encryption will become standard practices, reducing attack surfaces. Moreover, collaboration across industries through information-sharing platforms will enhance collective defense. The adoption of predictive analytics will enable SOCs to anticipate attacks before they occur. As cyber threats become more sophisticated, continuous innovation and investment in skilled personnel will be essential for maintaining effective security operations in the future.
Building a Resilient SOC for Security Excellence
Creating a resilient SOC involves integrating advanced technology, skilled personnel, and robust processes to form a comprehensive cybersecurity defense. Regular assessment and updates of security tools and policies are essential to adapt to emerging threats. Building a proactive culture of security awareness within the organization enhances overall resilience. Investing in ongoing training and certifications for SOC staff ensures they remain capable of handling sophisticated cyberattacks. Collaboration with external threat intelligence communities can provide early warnings of new threats. Automation and AI will streamline operations, reduce response times, and improve accuracy. Ultimately, a well-designed SOC acts as a strategic asset, enabling organizations to detect, respond to, and recover from cyber incidents swiftly, safeguarding their digital assets and reputation effectively.